Encrypted SIM Privacy - Complete Guide 2025
Every call you make, every text you send, and every time your phone pings a tower, information about you is logged. A standard SIM card does little to protect that trail. That’s why the idea of the encrypted SIM card has gained attention: a tool promising stronger privacy on mobile networks.
But here’s the truth — an encrypted SIM isn’t magic, and it isn’t marketing fluff either. It’s a powerful layer of defense with real benefits, and some hard limits. In this guide, we’ll cut through the myths, show you exactly what an encrypted SIM does for your privacy, and help you decide if it’s worth it.
Why Privacy on Mobile Networks Matters
Your phone is more than a communication device — it’s a tracking beacon. Every time it connects to a cell tower, your IMSI (subscriber ID) and IMEI (device ID) are exposed. Carriers log your movements, attackers exploit weak points in SIM security, and surveillance tools like IMSI catchers can follow you in real time.
Most people assume a regular SIM card keeps them safe because networks use encryption. In reality, that protection is thin. Metadata — who you called, when, and where you were — is still collected and can be intercepted. Downgrade attacks can push your phone onto older, insecure networks. And exploits like SIMjacker have proven that even text messages can be weaponized.
This is why the conversation around mobile privacy matters. The threats aren’t hypothetical. Journalists, executives, and even everyday users have found themselves exposed through weaknesses in the SIM layer. If you’re asking yourself “why use an encrypted SIM?” the answer is simple: because the standard protections built into your phone aren’t enough.
Key takeaway: Without an encrypted SIM, your digital footprint is wide open. With one, you gain a critical layer of defense against the invisible tracking most people never think about.
How Encrypted SIM Privacy Actually Work
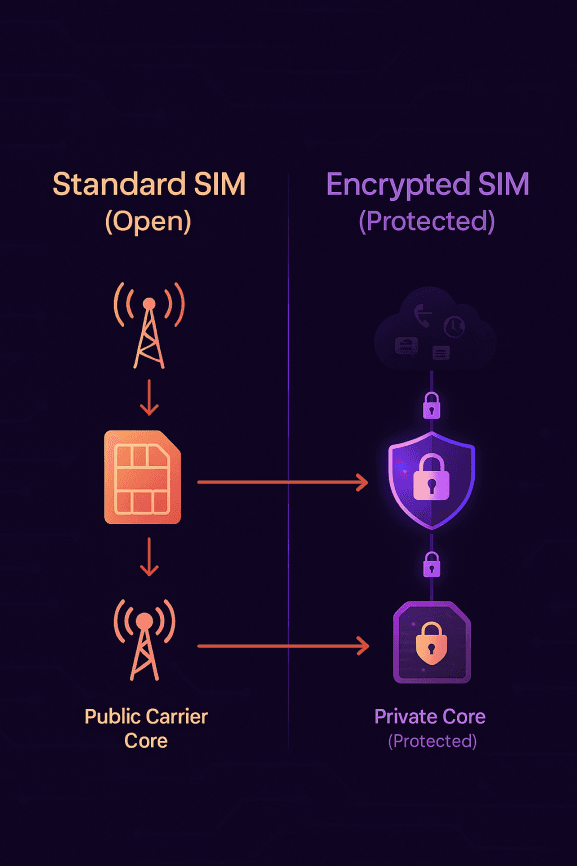
So what makes an encrypted SIM card different from the standard one sitting in most phones? It comes down to how the SIM interacts with the mobile network and the security controls layered on top. Here’s the plain-English breakdown:
Private Core Networks: A normal SIM connects through a public carrier core. A private SIM card routes traffic through a hardened, vendor-controlled core with added firewalls and monitoring. This reduces exposure to outside surveillance and signaling attacks.
IMSI Obfuscation: Your IMSI — the unique number tied to your identity — is the crown jewel for trackers. Many encrypted SIM solutions rotate or mask IMSIs to make passive tracking harder, especially against IMSI catchers.
Secure APNs: Instead of a public access point, encrypted SIMs use private APNs, creating a locked channel between your phone and the provider’s secure core. This helps isolate your traffic from standard carrier vulnerabilities.
SIM Toolkit Hardening: Exploits like SIMjacker showed how attackers could hijack the SIM Toolkit to push malicious commands. Encrypted SIMs disable or harden these functions, removing a key attack vector.
These encrypted SIM features don’t make you invisible, but they do give you control. Instead of relying on a carrier’s baseline protections, you’re putting your communications inside a controlled, security-first environment.
Key takeaway: If a regular SIM is like using the public highway with no locks on your car, an encrypted SIM is like moving into a gated, monitored lane — still visible, but much harder to attack.
Myths About Encrypted SIMs Privacy (And the Reality)
Whenever new privacy tools enter the market, hype tends to run ahead of reality. Encrypted SIM cards are no different. They’re powerful, but only when understood for what they are — and what they’re not. Let’s break down the most common encrypted SIM myths and set the record straight.
Myth 1 – An Encrypted SIM Makes You Invisible
When people hear about encrypted SIMs, the first thought is total invisibility. And while invisibility isn’t the right way to look at it, the truth is more exciting: an encrypted SIM gives you something much more practical — control over your privacy.
With IMSI obfuscation, private routing, and hardened SIM features, your communications become far more difficult for outsiders to intercept or trace. Instead of leaving an open trail every time you connect to the network, you operate inside a shielded environment that dramatically reduces exposure.
Think of it like tinted glass on a window — you can still see out, but it’s far harder for anyone to see in.
Myth 2 – You Don’t Need Anything Else
Another common myth is that once you have an encrypted SIM, you’re completely covered. The truth: an encrypted SIM is just one layer. It protects against network-level threats, but not against everything else that compromises privacy.
Malware on your phone, metadata harvested by apps, or tracking over insecure Wi-Fi are all outside the SIM’s control. That’s why the smart approach is not encrypted SIM vs VPN or encrypted SIM vs secure apps, but rather combining them. A VPN can encrypt your data plane, secure apps like Signal can protect your messages, and the encrypted SIM locks down the network identifiers. Each tool covers gaps the others leave open.
Key takeaway: Believing the myths creates false confidence. Recognizing the encrypted SIM limitations lets you build a layered defense that actually works.
What Encrypted SIMs Protect You From
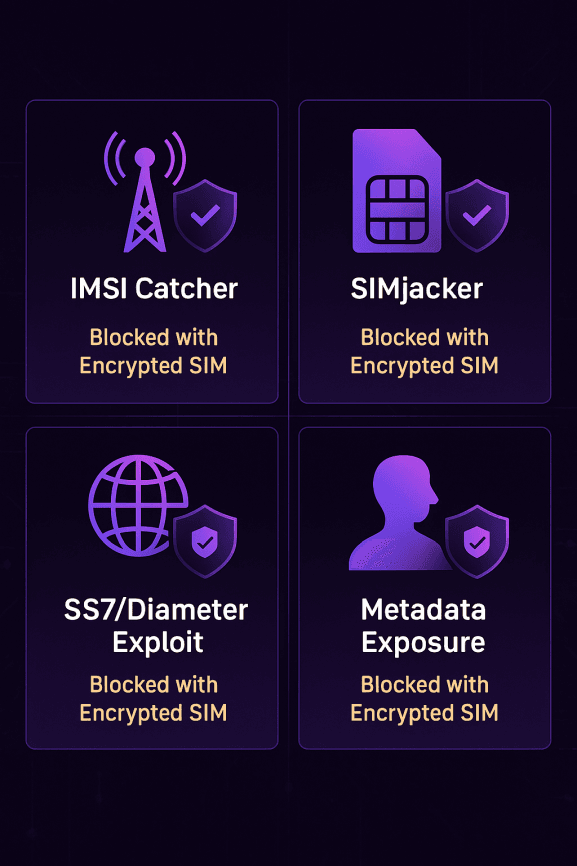
The real strength of an encrypted SIM lies in how it shields you from the kinds of network-level threats most people don’t even realize exist. These aren’t abstract risks — they’re proven methods attackers and surveillance tools use every day. Here’s what a properly designed encrypted SIM helps you avoid:
IMSI Catchers & Downgrade Attacks
Rogue devices called IMSI catchers mimic cell towers, tricking your phone into connecting and handing over identifying details. Encrypted SIMs add IMSI catcher protection by masking subscriber identities and resisting forced downgrades to older, weaker networks like 2G.SIMjacker Toolkit Exploits
The SIM Toolkit has been abused in the past to send hidden commands to phones — a technique known as SIMjacker. With hardened SIM configurations, encrypted SIMs neutralize these commands, blocking attackers from remotely taking control of functions like calls or messages.SS7/Diameter Interception
Global signaling protocols like SS7 and Diameter were never built with modern security in mind, which is why they’re exploited for surveillance and call interception. Encrypted SIMs route your traffic through private cores and firewalls, adding a critical layer of SS7 exploit prevention.Caller ID Spoofing & Metadata Exposure
Ordinary SIMs leak call details, message headers, and location data as metadata. Encrypted SIMs minimize this leakage, reducing the breadcrumbs outsiders can follow to map your movements or connections.
Key takeaway: An encrypted SIM is your frontline defense against silent, invisible attacks that standard SIMs simply weren’t built to resist.
Who Should Consider an Encrypted SIM?

Not everyone needs an encrypted SIM, but for certain groups, it’s a game-changer. If you fall into any of these categories, the benefits of an encrypted SIM are clear:
Executives & Business Leaders
High-level decision makers are prime targets for corporate espionage. An encrypted SIM reduces exposure to surveillance, protecting sensitive calls and travel movements.Journalists & Activists
Working in environments where information is closely monitored can put lives at risk. An encrypted SIM gives these professionals an essential safeguard, helping them communicate more freely and securely.Frequent Travelers
Crossing borders and roaming through unfamiliar networks often increases vulnerability. An encrypted SIM keeps privacy consistent, even when switching between regions with weaker telecom security.Privacy-Conscious Professionals
Lawyers, consultants, and others who handle confidential client data benefit from the extra assurance of stronger network security. For them, an encrypted SIM isn’t a luxury — it’s professional due diligence.
Key takeaway: If your role, travels, or responsibilities make your communications a valuable target, the question isn’t if you need an encrypted SIM — it’s how quickly you should make the switch.
GhostSims’ Approach: Privacy Without the Hype
At GhostSims, we take a simple stance: privacy should be practical, not overpromised. Many providers in the market push “anonymous” solutions that sound good on paper but rarely hold up in the real world. Our focus is on delivering encrypted SIM features that defend against real threats while staying transparent about what they do best.
Every GhostSims encrypted SIM is built on a secure private core with signaling firewalls that block common exploits. IMSI obfuscation helps protect against trackers, while hardened SIM Toolkit settings reduce exposure to SIMjacker-style attacks. Unlike generic carriers, our role as a private SIM provider means we put security first, building environments that make interception dramatically harder.
Our promise: No scare tactics. No inflated claims. Just a straightforward solution that gives you more control over your privacy in a world where mobile networks are designed to collect and expose your data.
Ready to switch to greater privacy? Order your Encrypted Sim today. Shipped worldwide and protects in over 200 countries.
FAQs
What does an encrypted SIM protect?
An encrypted SIM protects your mobile identity from common threats like IMSI catchers, SS7 exploits, and SIMjacker attacks. It reduces the metadata trails ordinary SIMs leave behind, giving you stronger privacy on the network level.
Do I still need a VPN with an encrypted SIM?
Yes — because an encrypted SIM and a VPN cover different layers. The SIM shields your mobile identifiers and signaling traffic, while a VPN protects your internet browsing and data streams. Used together, they give you a complete privacy strategy.
Key takeaway: These answers cut through confusion — an encrypted SIM explained in simple terms: strong against network-level attacks, complementary with VPNs, and best used alongside good security practices.
Conclusion
In a world where every call, text, and location ping is tracked, adding an extra layer of defense is no longer optional — it’s essential. An encrypted SIM gives you real control over your mobile privacy. From protecting against IMSI catchers to reducing metadata exposure, it closes gaps that standard SIMs leave wide open.
At GhostSims, we design encrypted SIMs with one focus: practical security that works. No hype, no empty promises — just the tools you need to make interception and surveillance dramatically harder. If privacy matters to you, a GhostSims encrypted SIM is one of the most effective steps you can take today.
Take the next step in protecting your privacy. Explore how a GhostSims Encrypted SIM can keep your communications secure and your data under your control. Discover GhostSims Encrypted SIMs →
Ready to Protect Your Privacy?
Get military-grade encrypted SIM cards with IMSI masking, end-to-end encryption, and true no-log privacy. Start protecting your communications today.
Related Articles

eSIM vs Physical SIM: Which Is More Private in 2026? (Reality Check)

SS7 & Diameter Attacks Explained: How Telecom Networks Leak Your Location and Calls