Imagine waking up tomorrow and realizing your phone number no longer belongs to you. No calls. No texts. And worse — someone else is receiving your bank verification codes, resetting your passwords, and draining your accounts while you’re left staring at a “No Service” icon.
That’s the terrifying reality of SIM swapping, one of the fastest-growing cybercrimes in the world today. Criminals don’t need to steal your phone — they only need to hijack the tiny chip inside it that controls your identity with your carrier. Once they succeed, your money, your personal data, even your reputation are suddenly at risk.
Most guides will tell you to set stronger passwords or add a PIN with your carrier. That’s important, but let’s be honest: if hackers can fool entire telecom companies, a simple PIN isn’t enough.
This is where GhostSims changes the game. With encrypted SIM technology, we don’t just make it harder for attackers — we make SIM swapping practically useless against you.
Read on, and you’ll discover how SIM swapping works, how to spot it, and the one step that puts you back in control.
Understanding the Basics
What is a SIM and Why Does it Matter?
That little plastic chip inside your phone may look harmless, but it’s the master key to your digital life.
A SIM (Subscriber Identity Module) does three critical things:
Identity – It tells your mobile carrier, “Yes, this is really you.”
Connectivity – It gives you access to calls, texts, and mobile data.
Verification – It delivers the one-time passcodes banks, apps, and websites use to double-check your identity.
That means every time you log into your bank, verify a payment, or reset a password, your SIM is involved.
And that’s exactly why criminals target it. Whoever controls your SIM controls your number. And whoever controls your number can impersonate you everywhere that matters.
What is SIM Swapping (SIM Jacking)?
SIM swapping (also called SIM hijacking) is when a criminal tricks your mobile carrier into transferring your phone number to a SIM card they control.
Unlike phishing scams that try to steal your passwords, or malware that infects your device, SIM swapping is even more dangerous because it bypasses one of the very safeguards meant to protect you: SMS-based two-factor authentication (2FA).
Think about it — you might have the strongest password in the world. But if your bank sends a verification code via text, and a hacker already controls your SIM, they don’t need your password. They already have the key.
That’s why SIM swapping has become the attack of choice for cybercriminals — it goes straight for the jugular of digital security.
How SIM Swapping Works
So how does a criminal actually steal your phone number? The process is disturbingly simple — and that’s what makes it so dangerous.
Here’s the playbook:
Collect your personal info – Hackers dig through data breaches, social media, and phishing emails to grab your birthday, address, even copies of your ID. You’d be shocked how much of this information is already floating around online.
Contact your carrier – Pretending to be you, they call or chat with your mobile provider. Armed with stolen data, they answer security questions with ease.
Convince the carrier to switch your number – They claim they “lost their phone” or “need a replacement SIM.” The rep, believing the story, activates a new SIM card — the one controlled by the attacker.
Take control of your digital life – From that moment, every text message and call meant for you goes straight to them. Password resets? Bank alerts? Crypto wallet codes? All in the hands of a criminal.
The Tools of the Trade
Phishing emails & fake websites trick you into giving up sensitive details.
Massive data breaches leak millions of personal records.
Insider threats involve rogue carrier employees selling access.
Forged documents like IDs or utility bills can be used to “prove” identity.
Real-World Example
In 2019, a college student in the U.S. stole over $5 million in cryptocurrency through SIM swapping attacks on multiple victims. His method? The same step-by-step process above — just repeated on a larger scale.
The scary truth is, these attacks don’t require elite hacking skills. They only require persistence, a little charm with a carrier rep, and access to your personal data.
Red Flags – Signs Your SIM Has Been Hijacked
SIM swapping doesn’t announce itself with sirens and flashing lights. Most victims realize too late — after money vanishes or accounts are hijacked. But if you know the warning signs, you can catch it in time to fight back.
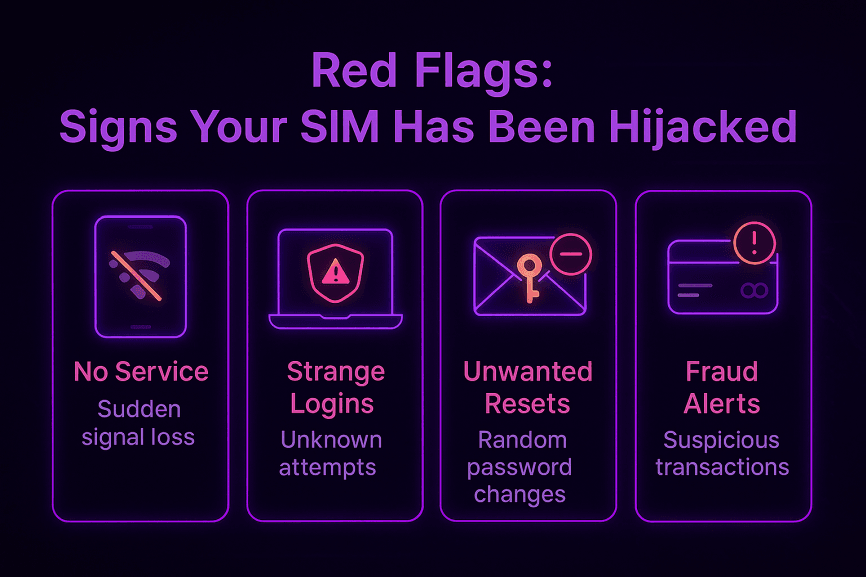
Here’s what to watch for:
No Service, No Signal – Your phone suddenly drops off the network for no reason. If you’re in an area with coverage and your phone reads “Emergency Calls Only,” that’s a huge red flag.
Strange Login Attempts – Emails or push alerts about suspicious logins, especially from locations you don’t recognize, mean someone’s already trying to get in.
Password Resets You Didn’t Request – If you start receiving “your password has been changed” or “reset link requested” emails out of nowhere, chances are a hacker is working with your number.
Unexpected Financial Alerts – Texts from your bank about withdrawals, purchases, or transfers you didn’t authorize are an urgent sign of fraud in progress.
If even one of these symptoms shows up, treat it like a fire alarm. The faster you act, the more damage you can stop.
Immediate Response – What to Do If You’re a Victim
When SIM swapping hits, every second counts. The difference between losing a few minutes of service and losing your life savings often comes down to how quickly you act.
Here’s your emergency playbook:
Contact Your Carrier Immediately
Call your mobile provider and tell them your number has been hijacked. Ask them to shut down the fraudulent SIM and restore service to your original card. Request that they lock your account to prevent further changes.Secure Your Email & Banking Accounts
Your email is the control room of your online identity. Change your email password first, then lock down your bank, PayPal, crypto wallets, and any financial accounts. Switch to app-based authentication wherever possible.Report the Fraud to Authorities
File a police report. Many banks and payment processors won’t investigate or reimburse stolen funds without one. If you’re in the U.S., report it to the FTC and your state attorney general as well.Monitor All Accounts Like a Hawk
Check your email, social media, and financial apps for suspicious activity. Hackers often keep probing even after you cut off their access — hoping you’ll relax and slip up.
Bottom line: Don’t panic, but don’t delay. Treat a SIM swap attack like a medical emergency for your digital life — swift action can stop the bleeding.
Why Social Media Makes You a Target

Think your Instagram feed is harmless? Think again. To a SIM swapper, your social media is a gold mine of free intelligence.
Every birthday post, tagged location, or “throwback” family picture is another puzzle piece they can use to impersonate you with your carrier. Oversharing doesn’t just entertain friends — it arms criminals.
Here are some of the most common traps:
Birthdays – That “Happy Birthday to me!” post? Hackers now have one of the most common identity verification answers.
Addresses & Locations – Posting from home, tagging your neighborhood, or even showing a utility bill in the background of a selfie? You just leaked your address.
Family & Pets – Cute pet names double as security answers (“What’s your first pet’s name?”). Hackers are paying attention.
How to Lock Down Your Digital Life
Tighten Privacy Settings – Make your profiles private and limit who can see personal posts.
Share Less, Later – Post travel photos after you return, not while you’re away.
Audit Your Content – Remove old posts that reveal addresses, birthdays, or sensitive details.
Remember: what seems like fun trivia to you can be the final clue a criminal needs to crack your digital identity.
Prevention Strategies That Actually Work
You don’t have to be powerless against SIM swapping. With the right habits and tools, you can make yourself a far tougher target. Let’s break it down.
Standard Best Practices
Set a Carrier PIN or Password
Most mobile providers allow you to add a secret PIN to your account. Without it, no changes can be made. It’s not bulletproof, but it’s a strong first barrier.Use Authenticator Apps, Not SMS Codes
Instead of relying on text messages for two-factor authentication (2FA), switch to app-based authenticators like Google Authenticator or Authy. Even if your SIM is compromised, those codes stay safe.Strong, Unique Passwords
If you’re reusing the same password across accounts, you’re doing hackers a favor. Use unique passwords for each service — and consider a password manager to keep them organized.Enable Alerts and Monitor Accounts
Turn on every notification your bank, email provider, and carrier will give you. An unexpected login or account change alert could be your first warning sign.
The Limits of Traditional Protection
But here’s the hard truth: even if you do everything right, these standard measures only go so far.
Carriers can still be tricked. Customer support agents are human — and social engineers are masters at sounding convincing. A PIN can be bypassed if an insider is bribed, or if a forged ID looks legitimate.
And SMS-based 2FA? It’s built on the very system criminals are attacking. If a hacker hijacks your SIM, your codes land straight in their hands.
That’s why relying only on traditional defenses is like locking your front door while leaving the back door wide open. You need a stronger layer — one that takes the SIM itself out of the equation for attackers.
Encrypted SIMs – A Next-Level Defense
Here’s the problem: traditional SIM cards were never designed with modern cybercrime in mind. They authenticate you, yes — but they don’t protect you. Once a carrier is tricked, a standard SIM card is helpless.
Encrypted SIMs change the rules.
Unlike regular SIMs, an encrypted SIM doesn’t just connect you to a network — it locks down your identity with advanced encryption that criminals can’t bypass through a phone call to customer service.
Why Encrypted SIMs Are Different
Encryption Built In – Your SIM data is scrambled and unreadable to outsiders, making cloning or hijacking virtually impossible.
Metadata Shielding – Not only are your calls and texts protected, but even the “who, when, and where” data is hidden, leaving attackers blind.
No Reliance on Carrier Security – Forget about begging your provider to keep you safe. Encrypted SIMs operate independently, putting control back in your hands.
Why GhostSims Leads the Way
At GhostSims, we don’t patch holes after the fact — we eliminate them. Our encrypted SIMs are designed for people who value privacy, security, and peace of mind above all else. Whether you’re protecting sensitive business data, financial accounts, or simply your personal identity, GhostSims gives you a level of defense carriers can’t offer.
Think of it as the missing piece in your SIM swap protection strategy. Passwords protect your accounts. 2FA protects your logins. But only an encrypted SIM protects the very foundation: your phone number itself.
With GhostSims, SIM swapping stops being a nightmare — and becomes a non-issue.
SIM Swap Fraud is Preventable
SIM swapping isn’t some unstoppable force of nature. It’s a crime that thrives on two things: lack of awareness and weak defenses.
Now you know the truth. You’ve seen how criminals operate, what red flags to watch for, and the best habits to keep your accounts safe. Combine that knowledge with smart security practices — and add the power of an encrypted SIM — and suddenly you’re no longer an easy target.
At GhostSims, we believe your phone number should belong to you and only you. That’s why we’ve built SIM technology that puts control back in your hands, shields your identity, and makes SIM swapping attacks practically useless.
The bottom line: SIM swap fraud is preventable. But prevention only works if you act before it happens.
Secure your SIM today with GhostSims — and take the worry of SIM swapping off your shoulders for good.
FAQs About SIM Swapping
What is SIM swap fraud?
SIM swap fraud happens when a criminal tricks your mobile carrier into transferring your phone number to a SIM card they control. Once they succeed, they can intercept your calls, texts, and verification codes — essentially taking over your digital life.
How do attackers pull it off?
They use stolen personal data, phishing tricks, forged documents, or even corrupt insiders at mobile companies to impersonate you. Then they convince your carrier to “activate” a new SIM — the one in their possession.
Can SIM swapping be stopped entirely?
Traditional methods like account PINs and app-based 2FA make it harder, but not foolproof. The only way to make SIM swapping practically useless is to use an encrypted SIM, which locks down your identity and resists carrier-level manipulation.
Are encrypted SIMs different from regular SIMs?
Yes — completely. Regular SIMs rely on your carrier’s security. Encrypted SIMs add advanced encryption, metadata shielding, and independence from carrier systems. With GhostSims, you control the lock on your phone identity.
Is SIM swapping the same as phone cloning?
Not quite. Phone cloning copies the data from one device to another. SIM swapping hijacks your number at the network level. Both are dangerous, but SIM swapping is especially effective at bypassing SMS-based security.
Conclusion
SIM swap fraud isn’t a minor inconvenience — it’s a direct attack on your money, your accounts, and your digital identity. Once a criminal has your number, they can tear through the safeguards you thought were protecting you. The danger is real, and the damage can be devastating.
But you don’t have to wait to become another statistic. With the right knowledge, smart security habits, and the protection of a GhostSims encrypted SIM, you can take control before hackers ever get the chance.
Think of it as locking the front door to your entire online life — once it’s secured, the rest of your defenses stand strong.
Don’t wait until your identity is hijacked—secure your phone with GhostSims today.
Ready to Protect Your Privacy?
Get military-grade encrypted SIM cards with IMSI masking, end-to-end encryption, and true no-log privacy. Start protecting your communications today.




