Before You Trust Your SIM, Read This
Most people think SIM hijacking and SIM cloning are the same thing. They are not. And if you don’t know the difference, you could be leaving yourself wide open to two very different kinds of attacks.
In a SIM hijack, criminals trick your mobile carrier into handing over your phone number. Suddenly, they control your calls, your texts, and those one-time banking codes you depend on.
In SIM cloning, attackers copy the data from your SIM and create a duplicate. The scariest part? Your phone may keep working normally while someone else silently monitors your calls and activity.
Both attacks put your privacy, finances, and identity at risk. The good news? You don’t have to be an easy target. With encrypted SIMs and eSIMS from GhostSims, you can close the gaps hackers exploit and take back control of your mobile security.
What is SIM Hijacking?
Imagine waking up one morning and your phone has no signal. No calls. No texts. Nothing. At first, you might blame your carrier, but what’s really happening could be far worse. You may have just become the victim of SIM hijacking.
Also known as SIM swapping or SIM jacking, this attack happens when criminals convince your mobile provider to transfer your phone number onto a SIM card they control. They often use stolen personal information or smooth-talking social engineering tactics to trick customer support into approving the swap.
The result? Your SIM goes dead while theirs lights up. From that moment, they intercept your calls, your text messages, and those critical one-time passwords (OTPs) used for banking, email, and social media logins.
Victims have had their bank accounts drained, their crypto wallets emptied, and their social media accounts hijacked in just hours. SIM hijacking isn’t just a nuisance - it’s a full takeover of your digital identity.
What is SIM Cloning?
If SIM hijacking feels like a smash-and-grab robbery, SIM cloning is more like a stealth break-in. Instead of tricking your carrier, attackers go after the SIM card itself, making a duplicate copy that looks and acts just like yours.
Here’s how it works: every SIM card carries unique identifiers such as the IMSI (International Mobile Subscriber Identity) and the Ki (the secret authentication key). With the right tools - and sometimes just physical access to your phone for a few minutes - criminals can extract this data and program it onto another SIM.
The frightening part is that both cards can function at the same time. While your phone seems perfectly normal, the attacker’s cloned SIM silently mirrors your activity. They can intercept calls, read texts, and monitor your communications without raising any immediate red flags.
Unlike hijacking, which usually aims for fast financial fraud, SIM cloning is often used for espionage, surveillance, and corporate spying. It’s the kind of attack that can compromise not only individuals but entire organizations.
SIM Hijacking vs SIM Cloning - The Differences You Need To Be Aware of
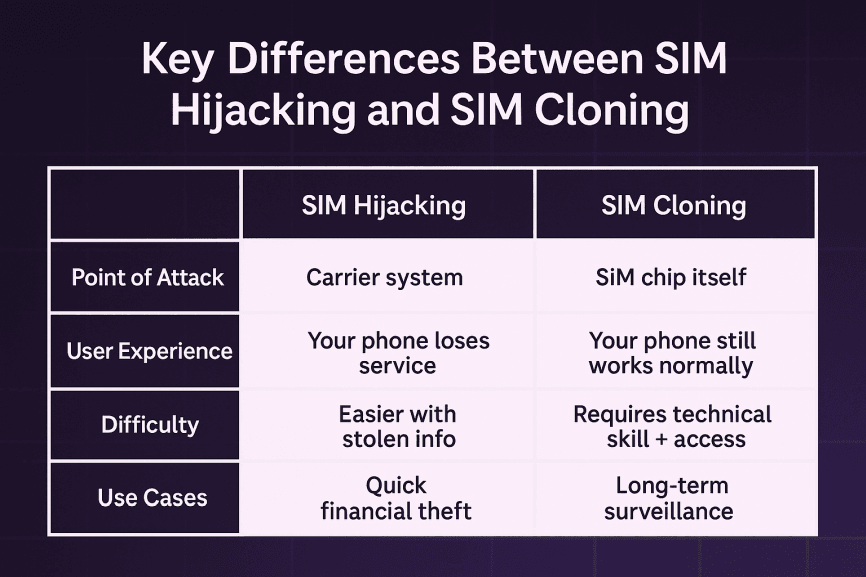
At first glance, SIM hijacking and SIM cloning may sound similar. Both attacks put your mobile identity at risk, but they operate in very different ways - and understanding those differences is critical if you want to protect yourself.
SIM hijacking strikes at the carrier level. Criminals rely on social engineering, tricking your provider into transferring your number to their SIM. The attack is often fast and loud: your phone suddenly loses service, and before you realize what’s happening, they’re draining bank accounts or hijacking your social media.
SIM cloning, on the other hand, is a technical duplication of your SIM card. Attackers extract unique identifiers like IMSI and Ki, then copy them onto another SIM. The clone works in parallel with your original, which means your phone may continue to function normally while someone else secretly eavesdrops on your calls and texts.
One is designed for quick financial theft, while the other is often used for long-term surveillance. Both are dangerous, but for very different reasons.
Feature
SIM Hijacking
SIM Cloning
Point of Attack
Carrier system
SIM chip itself
User Experience
Phone loses service
Phone still works normally
Difficulty
Easier with stolen info
Requires technical skill + access
Common Goal
Quick financial theft
Long-term surveillance/espionage
Both methods highlight one reality: standard SIM cards were never designed for today’s threat landscape.
Real-World Consequences
The fallout from SIM-based attacks isn’t just technical, it’s deeply personal and, in many cases, financially devastating.
With SIM hijacking, criminals often go straight for the money. Crypto investors have seen entire wallets drained overnight. Bank accounts are emptied within hours once attackers intercept one-time passwords. Even social media accounts aren’t safe; once hijacked, they can be used to scam friends, damage reputations, or lock victims out permanently.
SIM cloning, while less obvious, can be even more dangerous over time. Duplicated SIMs have been used in espionage cases, allowing spies to monitor communications without tipping off the target. Corporations risk losing intellectual property, trade secrets, or sensitive negotiations. Journalists and activists have also been targeted, with cloned SIMs exposing their sources and private networks to hostile actors.
Whether it’s the immediate financial loss of hijacking or the silent surveillance of cloning, the damage extends far beyond the SIM card itself. These attacks can destroy finances, erode trust, and compromise personal and professional security in ways that are difficult to recover from.
How to Protect Yourself
The good news is that you don’t have to sit back and hope you’re not a target. By taking a few proactive steps, you can dramatically reduce your risk from both SIM hijacking and SIM cloning.

Protecting Against SIM Hijacking
Start by locking down your carrier account. Most providers allow you to set up a PIN or password that must be provided before any SIM change request is approved. Without it, attackers will have a harder time impersonating you.
Next, move away from SMS-based two-factor authentication (2FA). Instead, use an authenticator app like Google Authenticator or Authy, which generates codes directly on your device and cannot be intercepted via a SIM swap. Finally, keep a close eye on your accounts for unusual activity - the faster you catch it, the faster you can shut down an attack.
Protecting Against SIM Cloning
Cloning usually requires some form of physical or technical access to your SIM card. That means your first line of defense is keeping your phone safe. Never hand it to untrusted repair shops or connect it to unknown SIM readers. For higher-risk individuals or businesses, consider upgrading to encrypted SIM technology, which makes it much harder for attackers to copy sensitive identifiers like IMSI and Ki.
Shared Defense
Both hijacking and cloning exploit weaknesses in traditional SIMs. Encrypted SIMs close many of these gaps by shielding your communications, blocking IMSI catchers, and hiding metadata that attackers rely on. For anyone serious about mobile security, they provide the most effective long-term protection available.
How Encrypted SIMs Help
Both SIM hijacking and SIM cloning share a common weakness: they exploit the fact that standard SIM cards were never designed with today’s threats in mind. Traditional SIMs expose your number, your metadata, and your communications in ways that make you an easy target.
This is where encrypted SIMs from GhostSims change the game. By adding a hardened layer of security, they make it far more difficult for attackers to succeed.
Protection against interception: Encrypted SIMs secure your calls, texts, and data traffic, ensuring they can’t be easily read or redirected, even if criminals attempt a SIM swap.
Metadata shielding: Instead of exposing who you’re contacting, when, and from where, encrypted SIMs obscure these details, shutting down one of the most valuable assets attackers and surveillance actors rely on.
Defense against IMSI catchers: Devices like Stingrays are designed to trick your phone into connecting so your identity and traffic can be monitored. GhostSims encrypted SIMs resist these traps, keeping your activity private.
The truth is, no single solution can make you 100% invincible. But encrypted SIMs dramatically reduce your attack surface, making both hijacking and cloning far less likely to succeed. For individuals and businesses that can’t afford to gamble with privacy, GhostSims is the proactive choice.
Final Thoughts
SIM hijacking and SIM cloning may look different on the surface, but both are serious threats. One relies on tricking your carrier, the other on duplicating your SIM - and either can leave your finances, privacy, and reputation exposed.
The key to staying safe is a mix of good security habits and stronger tools. Lock down your accounts, use app-based authentication, and be cautious with your personal information. But most importantly, upgrade the very foundation of your mobile security.
Discover how GhostSims encrypted SIMs can protect your communications and privacy today
FAQs
Is SIM cloning still possible in 2025?
Yes. While carriers and manufacturers have improved SIM security over the years, cloning remains possible with the right tools and access. Attackers who gain physical possession of your SIM - even briefly - can extract data to create a duplicate. This is why extra layers of protection, like encrypted SIMs, are becoming more important.
How do I know if my SIM has been cloned?
Unlike SIM hijacking, which cuts off your service, SIM cloning is harder to spot because your phone often keeps working normally. Warning signs include unexpected call or text activity on your account, sudden data spikes, or reports from contacts that they reached you when you never answered.
Can encrypted SIMs stop both hijacking and cloning?
Encrypted SIMs don’t make you invincible, but they dramatically reduce the risks. By shielding identifiers, encrypting communication, and defending against IMSI catchers, they make it far more difficult for attackers to hijack or duplicate your SIM data.
Which is more dangerous - SIM hijacking or SIM cloning?
Both are dangerous in different ways. Hijacking often leads to quick financial theft, while cloning is typically used for long-term surveillance. Either can have devastating consequences depending on the target.
Ready to Protect Your Privacy?
Get military-grade encrypted SIM cards with IMSI masking, end-to-end encryption, and true no-log privacy. Start protecting your communications today.




