What Is an Encrypted SIM Card? How It Works, What It Protects, and Its Real Limits
In a world where surveillance, SIM swaps, and location tracking have become everyday threats, the humble SIM card is no longer just a chip that connects you to your network — it’s a potential vulnerability. That’s where encrypted SIM cards come in.
An encrypted SIM card is a specialized SIM that uses advanced cryptographic protections and private network infrastructure to make your calls, texts, and data sessions far harder to intercept. Unlike a standard SIM, which relies entirely on your carrier’s built-in security, an encrypted SIM adds extra layers: masking your identity (IMSI/IMEI), routing traffic through hardened private cores, and in some cases even scrambling voice at the source.
But here’s the catch: encrypted SIMs aren’t a silver bullet. They can protect against certain types of surveillance (like IMSI catchers or SS7 exploits) — but they won’t stop everything. Malware on your phone, phishing, or a determined law-enforcement request to a network operator can still compromise your privacy.
In this guide, we’ll break down:
How encrypted SIM cards actually work
What threats they defend against — and what they don’t
Who benefits most from using them
Legal, practical, and technical limits you need to know
By the end, you’ll have the clear, unvarnished truth about encrypted SIMs — not just the marketing pitch.
Learn what encrypted SIMs are capable of for your privacy
TL;DR – Encrypted SIMs in a Nutshell
What they are: Encrypted SIM cards are specialized SIMs that add extra cryptographic protections and private routing layers beyond what a normal SIM card provides.
What they protect: They can shield you from some network-level threats like IMSI catchers, SS7 exploits, and basic interception attempts, while making your identity harder to trace.
What they don’t protect: They can’t stop phone malware, phishing, or lawful intercepts at the carrier level — so they’re a tool, not total invisibility.
Who uses them: Journalists, executives, frequent travelers, activists, and anyone operating in high-risk environments where privacy is critical.
The SIM Security Model in Plain English
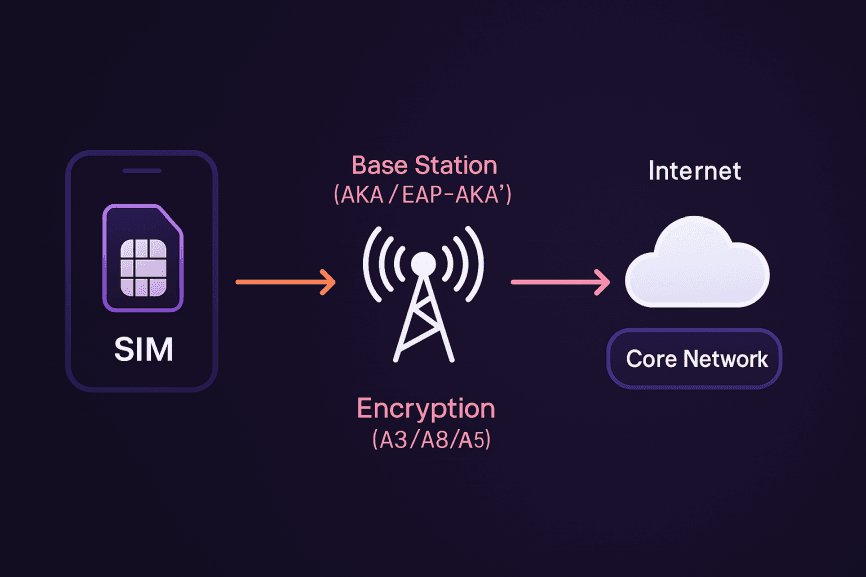
Before we can understand what an encrypted SIM card really does, it helps to know how a normal SIM already keeps you connected and (somewhat) secure.
Where a SIM Sits in the Stack
A SIM card is more than just a plastic chip — it’s a mini computer with secure memory that handles your identity on the mobile network. Here’s what happens behind the scenes:
HLR / AuC (Home Location Register & Authentication Center):
These are core database systems in your carrier’s network that store your unique ID (IMSI) and the secret keys linked to your SIM.Authentication & Key Agreement (AKA / EAP-AKA’):
Every time you connect, the SIM and the network run a “challenge-response” handshake. The network asks a question based on your secret key, and your SIM must answer correctly without ever revealing the key itself.A3 / A8 / A5 algorithms:
These are the cryptographic functions that generate authentication responses (A3), session keys (A8), and over-the-air encryption (A5). In practice, this means your calls and texts aren’t just plain radio waves — they’re scrambled using temporary keys.
In short: your regular SIM already handles identity, authentication, and session encryption whenever you connect to 2G, 3G, 4G, or 5G networks.
“Encrypted SIM” vs. Encryption Already in Cellular — What’s Actually Added
Here’s the catch: while cellular networks do use encryption, much of it depends on how the carrier implements security. Weak algorithms (like A5/1 in old 2G) and network loopholes (like SS7 signaling flaws) still allow interception.
An encrypted SIM card goes beyond the standard:
Private Core Routing: Instead of only using your carrier’s core, traffic is often routed through a private, hardened infrastructure with stricter firewalls.
Stronger Cryptography: Some providers implement end-to-end AES-256 or similar ciphers on top of the network’s default layer.
Identity Masking: Encrypted SIMs can obfuscate your IMSI/IMEI so devices like IMSI catchers can’t easily track you.
Secure Provisioning: In many cases, keys can be updated over-the-air using encrypted channels, reducing the risk of static keys being stolen.
In other words, the encrypted SIM doesn’t replace cellular security — it stacks additional protections on top of it.
What is IMSI Catcher? Read full details
How “Encrypted SIMs” Work (Vendor Patterns)
Not all encrypted SIM cards are built the same way. Different providers use different architectures and tricks to protect users — but most approaches fall into a few recognizable patterns.
Private MVNO/Core, SPLMN, and Private APNs
Some vendors, like SecureCrypt, build encrypted SIMs on top of a private mobile core network rather than relying entirely on a public carrier’s core.
SPLMN (Special Public Land Mobile Network): This acts like a private “mini-carrier” ID, allowing the SIM to register through custom Home Location Register (HLR) and Authentication Center (AuC) nodes.
Private APNs (Access Point Names): Instead of sending data through the public internet, traffic is forced through dedicated APNs with controlled gateways, VPN overlays, and SS7/Diameter firewalls.
Extra Filtering: These setups often block suspect signaling requests, SMS commands, or location updates that normal carriers would pass through.
In short, this approach gives the provider full control of the HLR/AuC/SGSN environment, reducing the risks of SS7 exploits and rogue network queries that plague public carrier infrastructure
Server-Assisted Features
Other vendors, like VipLine, emphasize feature-layer protections instead of deep network control. Their SIMs rely on application servers that sit between the SIM and the outside world.
Common features include:
Number Randomization: Each call can be routed through different outbound numbers, so your “real” number is never exposed.
Caller ID Masking: Outgoing calls show a proxy ID rather than your true identity.
Voice Morphing/Replacement: Some vendors even alter the pitch or digital profile of your voice to reduce recognition.
USSD Relays: Instead of direct dialing, calls are triggered via USSD sessions that bounce through an encrypted server layer, making interception more difficult.
This model is more about hiding metadata (numbers, identifiers, voiceprints) than changing how the underlying mobile network authenticates you.
IMSI/IMEI Handling — What Can Be Obfuscated vs What the RAN Still Sees
Every SIM has an IMSI (International Mobile Subscriber Identity), and every phone has an IMEI (International Mobile Equipment Identity). These are baked into the way mobile networks work, and they can’t just vanish.
IMSI Masking: Some encrypted SIMs assign rotating IMSIs or proxy identifiers that prevent passive tracking by IMSI catchers.
IMEI Concealment: Certain solutions attempt to randomize or spoof IMEIs, but this is limited since many carriers and 5G networks log device fingerprints for security and regulatory compliance.
Reality Check with 5G SUCI: In 5G, the permanent identifier (SUPI) is never broadcast directly. Instead, it’s concealed using SUCI (Subscription Concealed Identifier), which is encrypted with the home network’s public key (per ETSI/NIST standards). This greatly reduces exposure to IMSI catchers — but if the network is misconfigured or falls back to 4G/2G, the old risks reappear.
The bottom line: encrypted SIMs can make IMSI/IMEI harvesting harder, but they can’t completely erase the fact that networks still need to know who you are and what device you’re on. Their real value lies in adding more layers of obfuscation and reducing the attack surface.
Threats Encrypted SIMs Help With (and the Ones They Don’t)
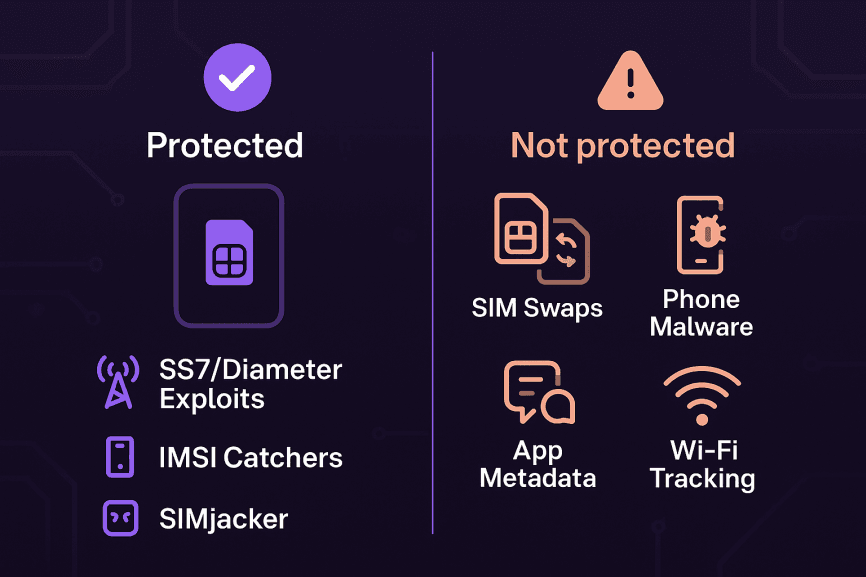
Encrypted SIM cards are often sold as “unhackable” — but the reality is more nuanced. They can strengthen your defenses against certain network-level attacks, yet they leave other risks completely untouched. Let’s break it down.
SS7/Diameter Exploitation & Signaling Firewalls
One of the biggest vulnerabilities in mobile networks lies in the signaling protocols — SS7 for 2G/3G and Diameter for 4G/5G. Attackers (or even state actors) can exploit these to:
Track a device’s location.
Intercept text messages.
Divert calls silently.
Vendors like SecureCrypt combat this by routing traffic through a private mobile core with hardened signaling firewalls. These block unauthorized queries, filter out suspicious location requests, and stop rogue operators from injecting malicious SS7/Diameter commands.
Bottom line: encrypted SIMs with private cores + firewalls can drastically cut signaling-based surveillance, something ordinary SIMs can’t protect you from.
IMSI Catchers, 4G/5G SUCI, and Downgrade to 2G Risks
IMSI catchers (a.k.a. stingrays) mimic cell towers to trick phones into revealing their IMSI — your unique subscriber ID. With that, attackers can track your movement or intercept communications.
4G and especially 5G improved this with the SUCI (Subscription Concealed Identifier) standard, which encrypts identifiers before they leave your phone.
However, flaws in implementation and downgrade attacks (forcing devices back onto weaker 2G/3G networks) can still expose you.
Encrypted SIMs add extra protection by rotating IMSIs, masking identifiers, or forcing connections to hardened network cores.
They can reduce exposure to IMSI catchers, but they cannot guarantee protection if your phone is coerced into using legacy 2G signals — a weakness highlighted by both academic researchers and security journalists at outlets like WIRED.
SIMjacker and SIM Toolkit SMS Control
The SIMjacker vulnerability showed that SIMs could be hijacked with a simple SMS containing hidden commands for the SIM Application Toolkit (STK). Once triggered, attackers could:
Track locations.
Intercept calls.
Execute commands directly on the SIM.
Reports from Enea and documentation on Wikipedia detail how this exploit targeted millions of SIM cards globally.
Encrypted SIMs can mitigate this risk by:
Hardening the SIM toolkit environment.
Filtering incoming OTA (over-the-air) messages at the private core before they ever reach your SIM.
This doesn’t make you bulletproof, but it shrinks one of the most underappreciated attack surfaces in the mobile ecosystem.
Find out what is Sim Jacking in detailed guide
What Encrypted SIMs Won’t Stop
It’s equally important to be clear on what encrypted SIMs cannot protect you from:
SIM Swap Fraud: Criminals can still socially engineer your carrier into transferring your number to their SIM — encrypted or not.
OS-Level Malware: Spyware like Pegasus operates at the device level, bypassing SIM protections entirely.
App Metadata & Cloud Services: Even if your SIM encrypts traffic, apps like WhatsApp, Google Maps, or social media still generate metadata that reveals who you are and what you’re doing.
Wi-Fi & Bluetooth Tracking: Encrypted SIMs only control cellular connections. Other radios (Wi-Fi, Bluetooth) remain potential tracking vectors.
As SecurityScorecard notes, true security comes from a layered approach — no single tool can replace good operational security practices.
Learn more about Sim Swapping and how to prevent it
Encrypted SIM vs. eSIM vs. Secure Apps vs. VPN
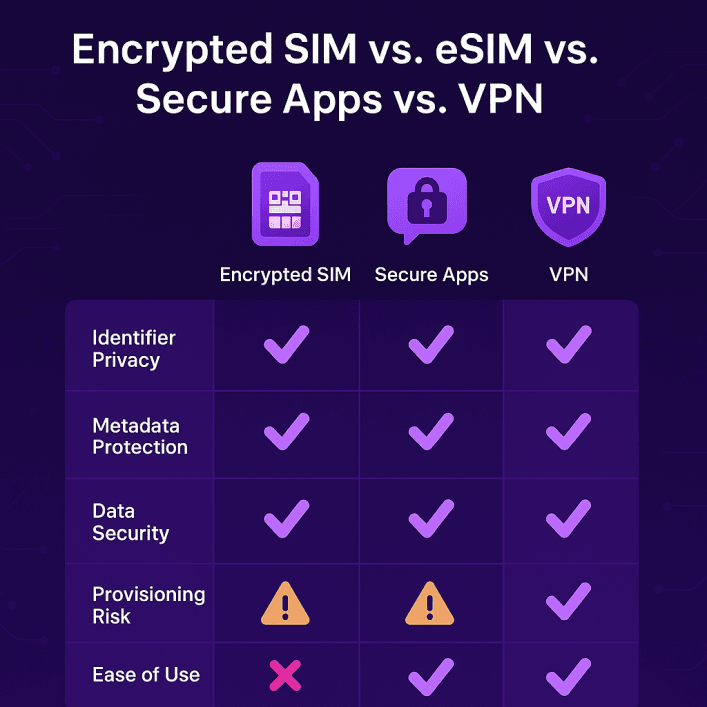
Encrypted SIMs are powerful, but they’re not the only privacy tool out there. eSIM technology, secure messaging apps, and VPNs all promise protection in different ways. To really understand their place, it helps to compare them side by side.
Feature / Risk AreaEncrypted SIMeSIM (carrier-based)Secure Apps (e.g. Signal, Proton, WhatsApp E2EE)VPN (e.g. NordVPN)Identifier Privacy (IMSI/IMEI exposure)
Can rotate or mask IMSI; helps vs IMSI catchers
Same IMSI, visible to network
App-level only, SIM still exposed
SIM still exposed; VPN doesn’t hide IMSICall/SMS Metadata (who you call, when, where)
Obfuscation possible (caller ID masking, private routing), but core still sees patterns
Carrier logs calls/SMS as normal
Carrier still sees metadata; only message content protected
Doesn’t hide who you call/text; only masks IP activityData Plane Security (internet traffic)
Routed through private APN / hardened core
Default carrier routing
Protects message body only; not other apps
Encrypts all IP traffic to VPN serverProvisioning Risk (SIM activation, cloning, remote updates)
Keys refreshed OTA; private AuC reduces carrier exposure
Standard carrier provisioning; depends on MNO
Not relevant at SIM level
Not relevant at SIM levelEase of Use
Requires provider & compatible phone
Built into modern devices
Simple app install
One-tap appsBest ForJournalists, executives, travelers in high-risk areasGeneral users who want convenienceProtecting conversations from interception
Public Wi-Fi security, masking browsing
activity
Takeaway: Only an encrypted SIM tackles the identifier problem (IMSI/IMEI exposure), which VPNs and apps ignore. But for end-to-end content protection, secure apps still beat any SIM-level encryption.
When to Combine
No one solution covers all threats. The strongest security posture comes from stacking tools smartly:
Encrypted SIM + Secure Apps → Protects against IMSI catchers and ensures your call/message content is encrypted (e.g. Signal, Proton, WhatsApp E2EE).
Encrypted SIM + VPN → Prevents identifier leakage while also hiding your browsing traffic from local ISPs or Wi-Fi operators (e.g. NordVPN).
eSIM + Private APN + E2EE Apps → A practical setup for frequent travelers using operators like Orange Travel, who want seamless roaming but still need privacy layers.
All Combined → For high-risk users, running an encrypted SIM, a VPN, and secure messaging apps in parallel gives multi-layered protection against both network and content-level surveillance.
Think of it like this:
Encrypted SIM = Protects who you are on the network.
VPN = Protects what you do online.
Secure Apps = Protect what you say and share.
eSIM = Adds convenience but not much extra security.
Learn more about Sim Cloning in this detailed guide
Legality & Compliance (Quick Guide, Non-Legal Advice)
Encrypted SIM cards often raise the question: are they even legal? The short answer: in most countries, yes — but the fine print depends heavily on local telecom regulations.
KYC/SIM Registration Regimes — When “Anonymous” Isn’t Truly Anonymous
Many countries require Know Your Customer (KYC) checks before a SIM can be activated. That means you must register with a valid ID, even if the SIM itself advertises “anonymity.”
Europe (e.g., UK, Germany, France): Mandatory SIM registration laws tie your SIM to your legal identity. Even if a vendor offers “encrypted” or “anonymous” SIMs, they often source them from jurisdictions with lighter rules, but roaming back into Europe means your usage is still logged.
United States: No federal requirement for prepaid SIM registration, but operators still log usage and can be compelled to share it.
Latin America & Africa: Mixed regimes — some countries have strict KYC, others are more flexible, making them hotbeds for anonymous SIM reselling.
Asia (e.g., India, Pakistan, China): Heavy SIM registration laws requiring biometric or government ID verification.
As Recharge.com points out, “anonymous SIM” marketing often oversimplifies reality. The carrier always has some visibility into your activity. Truly anonymous connectivity is rare and usually depends on jurisdiction loopholes.
Takeaway: If your SIM is linked to your identity at purchase, then by definition it isn’t fully anonymous — even if it uses extra encryption.
Law-Enforcement Visibility & Lawful Intercept Basics
Even with encrypted SIMs, law enforcement has tools to monitor communications when legally authorized.
Lawful Intercept Frameworks: Mobile operators worldwide are required by law (under ETSI and 3GPP standards) to provide interception capabilities for government agencies. That applies to both voice and data traffic.
Encrypted SIM Impact: While an encrypted SIM may hide identifiers, route traffic through private cores, or block signaling attacks, lawful intercept orders can still compel operators (or partner networks) to provide metadata and, in some cases, decrypted traffic if they control the endpoints.
Global Cooperation: Agencies can issue cross-border requests (MLATs) to get carrier records, so roaming doesn’t necessarily hide you.
Takeaway: Encrypted SIMs can reduce exposure to hackers, fraudsters, and mass surveillance — but they don’t make you “invisible” to lawful requests. They’re a privacy enhancement tool, not a way to bypass the law.
Who Actually Needs This?

Encrypted SIM cards aren’t for everyone. They’re built for people and organizations who face above-average risks — not for casual users who just want to browse Instagram more privately. Let’s break it down.
High-Risk Roles
Some groups genuinely benefit from the added protection and obfuscation that encrypted SIMs provide:
Journalists & Activists: Working in regions with heavy surveillance or censorship, where an exposed SIM could mean harassment, confiscation, or worse.
Politicians & Public Officials: High-profile figures are frequent targets for phone interception and location tracking.
Executives & High-Net-Worth Individuals (HNWIs): Corporate espionage, blackmail, and targeted fraud schemes often begin with a compromised phone line.
Frequent Travelers to Sensitive Regions: Roaming onto networks in countries with weak encryption or state-level interception practices.
Corporate Red-Teams & Security Professionals: Testing defenses or simulating attack scenarios where realistic anonymity and identifier protection are required.
In these cases, an encrypted SIM is less a luxury and more a layer of professional-grade OPSEC.
Who Doesn’t (and Cheaper Alternatives)
For everyday users, an encrypted SIM may be overkill. Most risks they face — spam calls, phishing, account hacks — can be reduced without expensive SIM tech.
Casual Smartphone Users: For general browsing and chatting, a VPN + secure messaging apps (Signal, WhatsApp E2EE, Proton) covers 90% of needs.
Small Businesses: Unless handling ultra-sensitive client data or operating in hostile environments, standard SIM security plus MFA (multi-factor authentication) and device hardening are sufficient.
Students & General Consumers: The privacy payoff usually doesn’t justify the cost. Encrypted SIMs won’t stop ad tracking, app data collection, or social media profiling anyway.
For most people, secure apps, VPNs, and good password hygiene give more bang for the buck than an encrypted SIM.
Which is best for privacy? VPN Vs Encrypted SIM Guide
Setup & Operational Hygiene
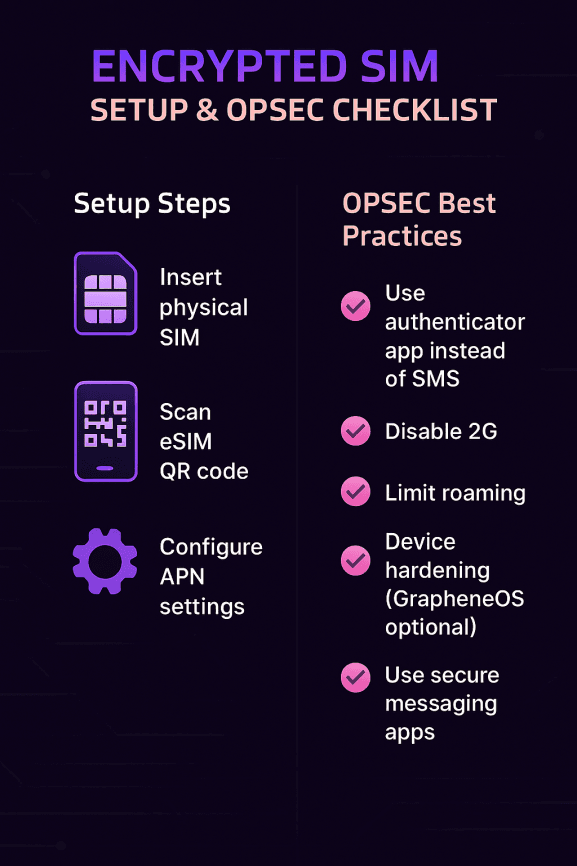
Buying an encrypted SIM is only half the story. To actually benefit from the extra security, you need to choose the right provider, set it up correctly, and follow good operational security (OPSEC) practices.
Choosing a Provider
Not all encrypted SIM vendors are equal. Look for providers that emphasize infrastructure-level security rather than just marketing buzzwords. For example, SecureCrypt highlights its private mobile core and signaling protection.
Key things to check:
Private Core Network: Does the vendor run its own HLR/AuC/SGSN, or do they piggyback entirely on a standard carrier? A private core reduces exposure to third-party surveillance.
SS7/Diameter Filtering: Critical for blocking malicious location tracking and call interception requests.
OTA (Over-the-Air) Key Management: The ability to refresh encryption keys remotely helps protect against long-term key compromise.
SIM-Toolkit Hardening: Vulnerabilities like Simjacker exploited weak SIM Toolkits. Ask whether the provider audits and restricts STK functions.
Independent Audits: Look for third-party security reviews, not just vendor claims.
If a provider can’t clearly explain their architecture, they probably aren’t serious about security.
Step-by-Step Activation
Most encrypted SIMs activate much like a normal SIM — but with a few extra steps.
For a physical SIM card:
Insert the SIM into your phone.
Enter the provided PIN/PUK (these are often randomized for extra security).
Configure the private APN in your phone’s network settings.
Run any vendor-supplied USSD or activation codes.
Test calls, SMS, and data through the encrypted routing.
For an eSIM (QR-based):
Scan the vendor’s QR code in your phone’s eSIM settings.
Confirm the APN settings point to the encrypted/private APN.
Activate and verify connectivity.
Ensure fallback profiles (like a local carrier eSIM) don’t override encrypted routing.
Unlike a standard SIM, an encrypted SIM may require more hands-on setup — and that’s a good thing, since it means you control where your traffic flows.
OPSEC Checklist
Even with the best encrypted SIM, sloppy habits can undo your security. Here are must-do hygiene steps recommended by neutral security experts:
Use an Authenticator App, Not SMS for MFA: SIM swap fraud bypasses SMS-based two-factor authentication. Switch to apps like Google Authenticator, Authy, or hardware keys.
Disable 2G on Your Phone: Many IMSI catcher attacks force devices down to insecure 2G. Most modern phones let you block 2G under “Mobile Network” settings. (NIST guidance supports phasing out 2G entirely.)
Set Roaming Policies: Limit roaming where possible, especially in high-risk countries with weak telecom security.
Device Hardening: Keep your OS updated, disable unnecessary radios (Bluetooth/Wi-Fi when not in use), and consider privacy-focused OS options like GrapheneOS for high-threat users.
App Hygiene: Only use trusted, open-source secure messaging apps (Signal, Proton, Wire) and avoid apps with aggressive data harvesting.
Remember: an encrypted SIM is one layer. Real protection comes when you combine it with good device security and disciplined user habits.
Limitations, Trade-Offs, and Gotchas
Encrypted SIMs add valuable protection, but they’re not magic. Like any security tool, they come with compromises that buyers should understand before committing.
Coverage Quirks, Emergency Calling, Latency, Call-Back Issues, and Cost
Coverage Quirks: Because many encrypted SIMs operate as MVNOs (mobile virtual network operators) or route through private cores, coverage may not match your local carrier’s footprint. In some regions, you’ll see weaker signals or slower handoffs.
Emergency Calling: In certain countries, emergency calls (e.g., 911, 112) may fail or route incorrectly if the SIM relies on non-standard signaling paths. Always test in advance.
Latency: Private routing and extra encryption layers can add milliseconds to call setup and data sessions. For normal users, it’s unnoticeable — but for high-frequency traders or critical communications, delays matter.
Call-Back Issues: Features like number randomization or caller ID masking can sometimes break compatibility with services that expect a stable caller ID (banks, two-factor authentication via phone calls, etc.).
Cost: Encrypted SIMs are usually more expensive than regular SIMs — both upfront and in ongoing subscription fees. The extra infrastructure (private cores, security features) doesn’t come cheap.
Takeaway: Think of encrypted SIMs as a trade-off between stronger security and day-to-day convenience.
“IMEI/IMSI Hiding” Claims — What’s Accurate vs Marketing
Many vendors advertise their SIMs as “hiding your IMEI/IMSI completely.” This is often misleading.
IMSI (Subscriber Identity): Some providers (e.g., Encriptados.io) describe their SIMs as “masking your IMSI and IMEI,” but what they usually mean is that they rotate IMSIs or use proxy identifiers. The home network still authenticates you using a real IMSI — it just may not be exposed as plainly.
IMEI (Device Identity): While it’s possible to obfuscate or spoof IMEIs, in practice most carriers still log your device’s hardware fingerprint. An encrypted SIM cannot guarantee that your IMEI is invisible.
5G Reality Check: With 5G, the permanent subscriber identifier (SUPI) is concealed using SUCI encryption (per ETSI standards). This does improve anonymity, but fall-back to 4G/2G can still expose IMSIs — something no SIM vendor can fully prevent.
Takeaway: Encrypted SIMs make it harder to passively capture your identifiers, but they cannot erase them entirely. Be wary of any provider promising “total invisibility.”
GhostSims’ Approach
We’ve covered what encrypted SIMs are, how they work, and where they fall short. So where does GhostSims fit in? Our philosophy is simple: combine infrastructure-level security with practical usability.
Architecture Summary and Controls
Instead of relying only on “feature gimmicks,” GhostSims is built around the same pillars we’ve just discussed:
Private Core Network: Your traffic is routed through a hardened, private infrastructure — not left exposed on a public carrier core.
SS7/Diameter Protection: Signaling firewalls filter out malicious location requests and block suspicious call diversions.
IMSI Privacy: Our SIMs leverage identifier obfuscation and rotation strategies to reduce passive tracking risk, aligning with modern 5G SUCI standards.
OTA Key Management: Encryption keys can be refreshed securely over the air, reducing long-term compromise risks.
SIM Toolkit Hardening: STK functions are restricted and audited to neutralize threats like Simjacker.
The result is a SIM card designed for real-world threat models, not just marketing promises.
Learn more about how GhostSims can protect your communications on our Encrypted SIM product page
FAQs
Are encrypted SIMs legal in my country?
In most regions, encrypted SIM cards are legal, but they must comply with local telecom regulations. Many countries require SIM registration (KYC), which ties the SIM to your identity even if it offers extra privacy. Always check your jurisdiction’s rules before purchase.
(Source: Recharge.com – Anonymous SIMs)
Can police track an encrypted SIM?
Yes — if law enforcement has a lawful intercept order, they can compel operators to share usage data. Encrypted SIMs make it harder for hackers or IMSI catchers to track you, but they don’t make you invisible to legal investigations.
(Source: ETSI lawful intercept standards; SecureCrypt signaling firewall documentation)
Do encrypted SIMs stop SIM swaps?
No. SIM swap fraud happens at the carrier level, when attackers socially engineer customer service into transferring your number. Encrypted SIMs protect against network-level surveillance, but they cannot stop account takeovers caused by SIM swap scams. Using an authenticator app or hardware key for MFA is the best defense.
(Source: SecurityScorecard – SIM Swap Risks)
What’s the difference between an encrypted SIM and PGP on my phone?
Encrypted SIM: Works at the network level, protecting identifiers (IMSI/IMEI) and routing traffic through hardened cores.
PGP (Pretty Good Privacy): Works at the application level, encrypting the content of your emails or messages.
The two tools solve different problems — one hides your network footprint, the other protects the content of your communication. Using both can provide stronger layered security.
(Source: Encriptados.io; NIST publications on IMSI/SUCI privacy)
Conclusion
Encrypted SIM cards are not a silver bullet, but they are a powerful tool for anyone who values privacy in an age of constant surveillance. They harden weak points in traditional mobile networks, protect against threats like IMSI catchers and SS7 exploits, and give high-risk users greater control over their communications. At the same time, they come with trade-offs: costs, setup requirements, and the reality that no SIM can protect against every risk.
At GhostSims, we believe in cutting through the hype and offering encrypted SIM solutions that are built on solid architecture, independent controls, and transparency about what these cards can — and can’t — do. If your work or lifestyle puts you in situations where privacy is more than just a convenience, GhostSims can provide the extra layer of protection you need.
Further Reading -
What Can an Encrypted SIM Really Do for Your Privacy? Myths vs Reality
What is SIM Jacking and Best Ways To Protect Your Privacy
What is an IMSI Catcher? How Encrypted SIMs Protect Your Privacy
How to Protect Your Phone from SIM Swapping
SIM Hijacking vs SIM Cloning: What’s the Difference?
Encrypted SIM vs VPN vs Secure Apps: Which Protects Your Privacy Best in 2025?
SIMjacker Explained – How Encrypted SIMs Block It
Why Executives and Journalists Use Encrypted SIMs: Privacy, Power, and Protection in 2025
Ready to Protect Your Privacy?
Get military-grade encrypted SIM cards with IMSI masking, end-to-end encryption, and true no-log privacy. Start protecting your communications today.




